Research Fields
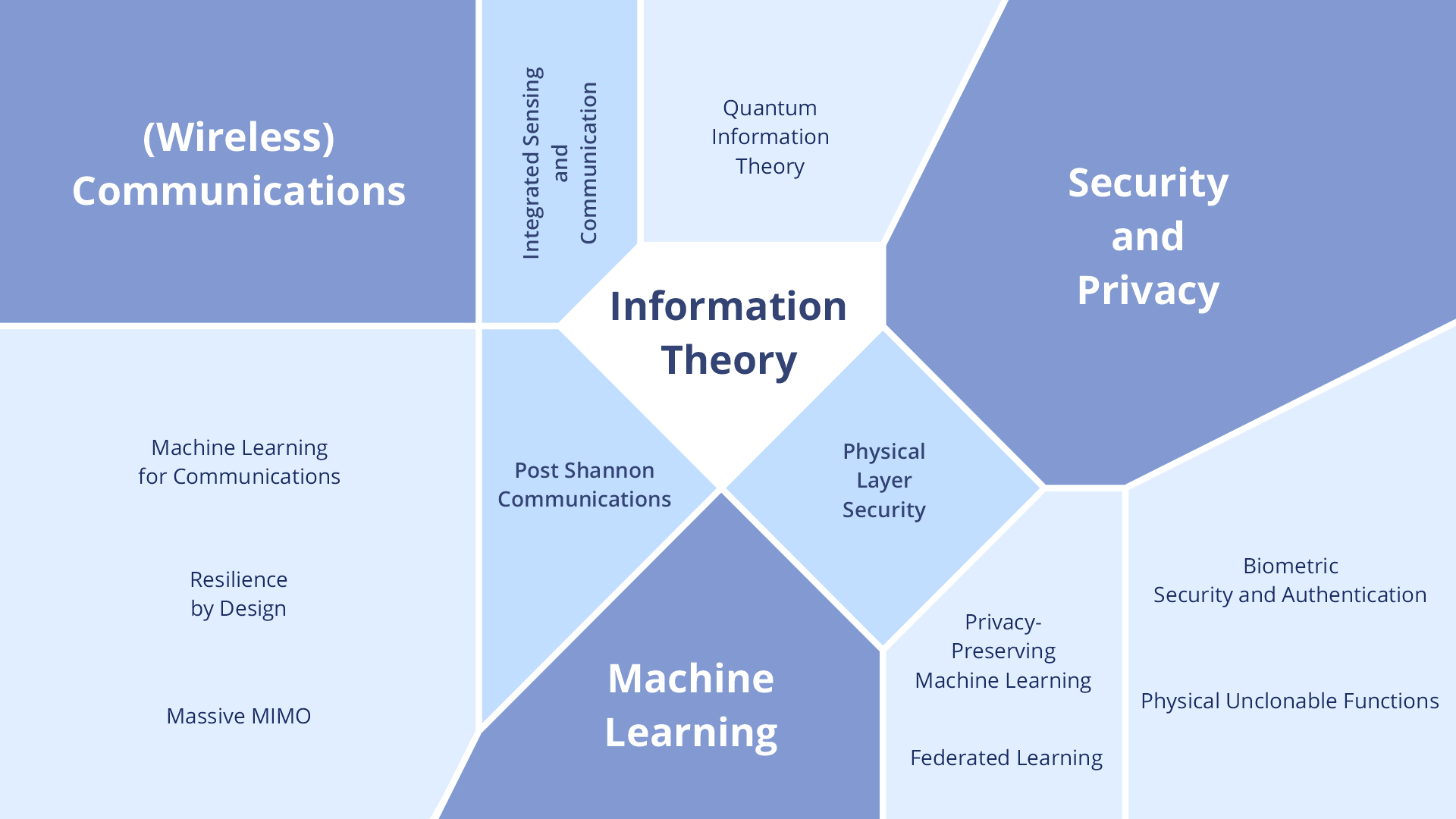
- (Wireless) Communications: On the path towards more capable communications standards, novel algorithms and technologies for data transmission promise improved performance with respect to data rates, latency, reliability, and energy efficiency. These include goal-oriented (Post-Shannon) communication that refers to a paradigm shift in which the recipient of a message is primarily interested in its semantic relevance and less in its pure content. Furthermore, the joint use of radio communication and (radar) sensing (Integrated Sensing and Communication) plays a major role in the optimization of networks with respect to their environment. For instance, the communication link can be improved by adaption to the propagation profile of the radio channel. In addition, we investigate the use of quantum technologies for future communication networks from an information-theoretic perspective.
- Security and Privacy: In today's communication systems, information security and privacy are made possible almost exclusively by encryption methods whose effectiveness is only guaranteed by the assumption that the adversary is limited in his computational resources. The majority of these procedures will become obsolete with the advent of quantum computers and thus represent an enormous security risk. In contrast, the information-theoretic view on security takes a different approach. It does not make any assumptions about the adversaries' computing capabilities, but quantifies security in terms of the information that is made available to the different parties. In particular, Physical Layer Security aims for an inherent guarantee of security by intelligent transceiver design, e. g., by exploiting the natural properties of the channel such as noise, which are traditionally regarded as hindrances for communication. The main focus in this field of research lies on secret key generation and channel coding for security. Our other research interests include the information-theoretic investigation of security and authentication schemes using biometric factors as well as so-called Physical Unclonable Functions. The latter are hardware components that have certain properties due to process variations in their production that can be harnessed for authentication or the generation of keys.
- Machine Learning: Novel machine learning techniques, e. g., diffusion models or autoencoders, are suitable for solving complex problems for which we lack precise analytical comprehension. Such approaches can also be used in communications, for instance, to model the behavior of the radio channel, to learn new schemes for channel coding or to quantify the amount of transmitted information. One aspect that often receives little attention concerns the data security of these methods, e. g., with regard to the privacy of training and inference data, which can reveal sensitive information about the user. Among others, this problem can be addressed by Federated Learning.
