Module und Lehrveranstaltungen
The Master's Program in Distributed Systems Engineering at TU Dresden requires you to complete modules, as opposed to only completing particular exercises or assignments. A module combines, for instance, lectures with tutorials or lab assignments and self-studies. A module sometimes may also consist of multiple exams, the results of which will be combined to an overall grade for the whole module. A module must be completed as a whole – you cannot pick only some parts / exams of a module since you cannot obtain partial credits. All modules have a code, such as INF-DSE-20-M-SE1 for the module Foundations of Systems Engineering. We distinguish mandatory (M), compulsory elective (E) as well as language modules (LN), which are listed below. For the sake of simplicity, the prefixes were ommited in the lists below.
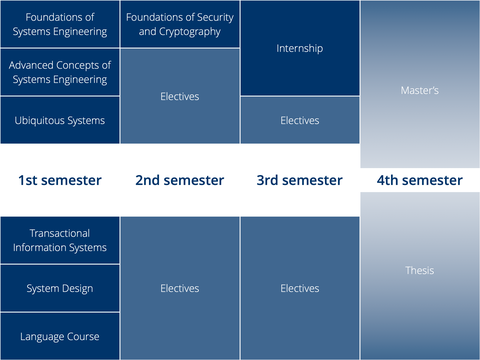
DSE Curriculum
Hereinafter you will find an overview of the curriculum of the international master's program in Distributed Systems Engineering. You'll start in the first semester with the mandatory modules,followed by two semester in which you choose your modules from the list of compulsory electives. The fourth semester is fully dedicated to writing the master's thesis. The mandatory internship is scheduled for the second semester but can be done at any time before you start your master's thesis.
Mandatory Modules
In order to establish strong foundations in the field of Distributed Systems, the currculum comprises six mandatory modules plus the mandatory internship which enables you to transfer the theoretical knowledge into practical experience. Except for the internship, which technically can be done at any time during the first three semesters, all mandatory modules are offered in the first semester.
After completing this module, students are able to architect distributed software platforms using modern hardware and software components. They are aware of challenges concerning programming and correct operation of such systems. Students are able to analyze and evaluate such systems.
After completing this module, students are able to architect highly scalable and distributable systems which usually run, for instance, in computing or data centers. They know principle, concepts and methodologies to implement and operate such systems.
This module will provide an overview of middleware architecture and platforms for the development of distributed applications and information systems. In doing so, the focus will be both on the intensive discussion of the field of mobile communication or mobile processing. The students will learn to identify and develop concepts and architectures for distributed and omnipresent applications, to choose appropriate solutions, and to evaluate modern technological developments in this field.
Lectures include:
- Distributed Systems: an introduction to problems, concepts and solutions of Distributed Systems. It covers basic principles such as the client/server model, remote procedure call, distributed object-oriented systems as well as current standards.
- Mobile Communication/Computing: an introduction to principles, standards and solutions for mobile communication and its applications within the area of mobile computing. Based on the physical foundations of mobile communication channels, typical standards such as GSM (Global System for Mobile Communication) are presented. Techniques for locating mobile users and mobile devices also present a major focus area. In the area of application support, typical software architectures and services for mobile computing are discussed. Examples of application areas covered are sales support and service engineering. An outlook towards high performance communication in mobile networks and related applications concludes the lecture.
Links:
Distributed Systems – Lecture Information
Mobile Communication and Mobile Computing – Lecture Information
Database systems play a central role in building large and distributed transactionally working information systems. Within this lecture, we discuss techniques that are required to set up a robust distributed information system. After repeating the core concepts of ER modeling and the relational database model, including SQL and object-relational extensions added within SQL:2003, we focus on different data models like network data model, object-oriented data model, and XML data model in combination with different database manipulation languages. Thereafter, we discuss concepts required in the area of distributed data management like 2-phase commit and core concepts of replication technology.
Students who complete this module are able to discuss further topics on the transactional processing in distributed environments (especially with regard to large information systems) and have a basic understanding of information systems.
Foundations of Security and Cryptography introduces the basic concepts of security and cryptography. Students who complete this module are able to discuss further topics on the construction of distributed and secure systems from the angle of data security and apply their knowledge in practical scenarios. They have a basic understanding of data security in distributed systems and have learned how to solve questions in this area on their own.
After having completed the module, students have learned how to apply basic methods, constructional elements and notations for the systematic development of large software systems and also the methodology of modelling and simulating discrete event systems. The framework of the module is based on the software development process with its life cycle models and phase models and additionally on the application of simulation and modelling techniques to the design of large and flexible application systems. Students who have completed the module are able to assist the development of large, consolidated, state-of-the-art software systems and to apply the methods of systems analysis to practical scenarios.
After having completed the module, students will be able to independently accomplish individual research projects that focus on the practical application of the skills acquired during studies to distributed systems. They will have learned to analyse complex tasks and work out efficient solutions. This will enable them to understand and discuss practical scenarios in their professional lives and find feasible solutions.
Students are encouraged to do an internship in industry related to the topics of Distributed Systems Engineering. However, students may alse choose among various labs (Komplexpraktikum) that are offered at the faculty of computer science.
The mandatory internship is an essential part of your studies. Though it is scheduled for the second semester you can do it whenever you want throughout your studies. Just make sure you complete it before the begin of your master thesis. We recommend not to start with the internship before you completed all mandatory modules. Moreover, we strongly recommend to do the internship in a company. Why? You should learn about real-life engineering aspects that cannot be taught in whole at universities. Real-life projects include large teams, code styling, complex code versioning, code reviews, achitecture discussions, and so on... This cannot be acomplished by a simple university lab.
Please check the website of the internship module for further details.
Compulsory Elective Modules
The international master's program on Distributed Systems Engineering offers you a variety of modules to choose from in order to fit you studies to your individual interests and needs. From the below list of modules you have to choose seven to eight modules to achieve in total 42 credit points. Check the study regulations for more details.
This module gives a thorough introduction to security in general and to multilateral security of IT-systems in particular. Protection goals and their interdependencies are discussed as well as reasonable attacker models. Different kinds of security mechanisms are introduced to provide examples and to clarify that security mechanisms are means to provide for protection goals against attackers at most as powerful as described in the attacker model. Cryptosystems are the fundamental security mechanisms to achieve the protection goals confidentiality and integrity in distributed IT-systems and are therefore discussed indepth: This module provides a classification of cryptosystems according to the protection goal they are aiming at and the key-distribution they use and it focuses on those cryptosystems whose security is as much validated as possible or even provable.
Students will be enabled both to define and analyze security properties of IT-systems in two respects: What security properties the IT-system is supposed to have and how sure we can be that it really has these properties with respect to could be attackers. In addition, basic knowledge is acquired and basic skills are developed how to construct secure IT-systems.
The course is especially for those students who are interested in ubiquitous computing and particularly in Wireless Sensor Networks. The course begins with an introduction to the application of wireless sensor networks and the main components which constitute wireless sensor networks. After wards, it investigates typical aspects of wireless sensor networks such as energy consumption, communications, in-network processing, and self-organisation. These aspects determine the type of architecture a given wireless sensor network should have. Following this, the course delves into the issues of link formation and medium access control in wireless sensor networks where a set of proposed algorithms will be investigated. Because a wireless sensor network is a distributed network, time synchronisation, topology control and data aggregation issues will also be treated in this course. Another aspect of the course is routing techniques and query distribution. These two issues will be treated in particular detail since they influence the life time of a wireless sensor network. The course will then investigate outstanding issues in wireless sensor networks.
The course aims to provide students from Bachelor to PhD level all skills required to conduct good scientific work. The goal is that after visiting the course, you should be able to write your thesis.
Depending on the level of the participants of the lecture, the contents will be adjusted. If all levels are represented in the course, there will be two parts: one for BA-and MA-level (incl. Diploma-level) and one for PhD-level students.
The lecture will be an open discussion instead of a frontup reading of slides. Thus, prepare for the lecture by reading them yourself. The lecture itself will be a guided discussion of the contents of the slides.
Link:
Academic Skills in Software Engineering - Lecture Information
Students will be able to design, develop, and debug system software that is directly based on hardware. They will be able to make design decisions that have a direct impact on the potential applications of the system by knowing the impact on non-functional emergent properties such as interrupt latencies.
The lecture provides conceptual foundations and key techniques for building an operating system. In the exercise accompanying the lecture, this knowledge is applied practically by developing a simple PC operating system from scratch in small working groups. To accomplish this, a sound knowledge of the structure and functioning of PC hardware is required, which will also be taught in the course. For example, the protection concept of the IA-64 architecture, current PC bus systems and modern multiprocessor interrupt systems are addressed. At the same time, basics from the operating system area such as interrupts, synchronization and scheduling, which should be largely known from previous courses, will be repeated and deepened.
Link:
Operating-System Construction (Betriebssystembau) – Lecture Information
Upon completion of the module, students have learned to solve complex problems of the design of distributed systems on their own, to analyse case studies and to make comparisons with other projects to identify potential critical issues. They can make argumentative points and defend them.
Moreover students are familiar with scalability, fault tolerance, security and robustness and can see things in context with issues, such as database development and computer architecture. Thanks to their broad knowledge, students can also assess the latest developments and discuss them.
Upon the successful completion of this module, students are able to face the challenges of modern complex software systems using a component-based development concept. They know how to build applications step by step using independent components and how to increase their flexibility. Thanks to very practical exercises, they are also capable of solving realistic tasks and to tackle new challenges on the basis of the sound fundamental skills they acquired.
Link:
Component-based Software Engineering - Lecture Information
Upon completion of the module, students have learned to understand and discuss general Internet technologies and protocols and also the technical basics and methodological principles. This includes traditional applications and protocols, such as HTTP or DNS and also more recent developments. Moreover, students understand innovative web applications and web technologies and can apply and extend them on their own. This applies not only to basic principles but also actual standards, systems and techniques, such as Web 2.0, Ajax, OWL, podcasts, blogs, Wikis, BitTorrent etc.
The lecture provides an introduction to concepts and tools for Internet measurements. In addition to basic concepts, we focus on the question how the Internet core and applications and services on top look like in real deployment. Using concrete examples, we illustrate how to measure common and emerging communication solutions (e.g., BGP, IPv6, DNSSEC, QUIC) and which limits exist. The topics presented in this course relate to network security and performance measurements. The lecture will be complemented by a lab in which you will conduct your own measurements and play with big data.
Most of the fundamental models underlying any artificial intelligence or machine learning rely on probabilistic estimation. In unsupervised learning, such as Tensor Decomposition, Principal Component Analysis, and Singular Value Decomposition, the analysis of multi-dimensional correlation is raw data is essential to uncover underlying features or patterns. Similarly, in voice recognition and synthesis, it is vital to examine state transitions and conditional dependencies. In complex computer networks, the dynamic prediction and/or estimation of various models and model parameters such as queue length, collision probability, traffic congestion, throughput is required to maintain resilient networks. The aim of this lecture is to provide students with the fundamental knowledge of probabilistic based estimation techniques. The course is intended to prepare graduate students and PhD candidates for advanced research.
Link:
Prediction and Estimation Techniques – Lecture Information
The course is especially for students which are interested in mobile computing applications and their implementation. The course starts with an introduction also to new areas like Ambient Intelligence and Ubiqitous Computing, describes applications and gives an overview about the domain.
After that, the next courses consider different functionalities such as networking aspects (different short and long range communication capabilities), and special mobile computing concepts such as disconnected and autonomous operation, mobile agents and context based adaptation. After that, different architectures for mobile distributed systems are discussed. Different options for implementing mobile systems, starting from communication, over local and distributed platforms (e.g. OSGi, J2ME, J2EE) until the implementation of graphical user interfaces are given in the implementation section of the course. Additional concepts such as mobile security, data synchronozation, downsizing of applications to mobile devices, data synchronization methods, databases for mobile devices, location based services, Semantic Web and autonomous behaviour will be partly discussed in a separate section. Tools, environments, platforms and emulators are considered near the end of the course, as well as current international research and industrial projects will be presented.
Link:
Engineering Adaptive Mobile Applications - Lecture Information
Upon completion of this module, students have a good understanding of the fundamentals of concurrent and distributed systems, which are necessary for the construction and operation of concurrent and distributed applications. They can work with transactional memory systems, which will be supported by most CPUs in the future.
Link:
Foundations of Concurrent and Distributed Systems - Lecture Information
In conjunction with Foundations of Concurrent and Distributed Systems, this module provides you with practical experience in this domain.
The root cause of many system outages are software bugs. This is particularly the case for distributed systems because distributed software is inherently more complex than traditional software for single processor systems. The complexity and economics of software and system development implies that software bugs will not be eliminated. Hence, designs and mechanisms that can deal with software bugs during runtime are needed. This module introduces a wide variety of software fault tolerance concepts and mechanisms.
In conjunction with Foundations of Software Fault Tolerance, this module provides an in-depth, hands-on experience in selected software fault tolerance mechanisms.
After successful completion of this module, the participants are able to comment on current developments in the field, evaluate them and independently search for, find and evaluate relevant literature. Furthermore, they have the ability to understand scientific articles, to process their contents and to present them.
Contents are offered each semester depending on current developments in the topics Software Fault Tolerance and Dependable Systems.
Links:
Current Topics in Software Fault Tolerance (Seminar) – Information
Current Topics in Dependable Systems (Seminar) – Information
The Roboblab Sessions are offered every year in the winter semester and are done in small groups. Challenges in the field of computer science will be solved by using practical programming tasks. The students will gain skills in programming as well as experiences in project and team work. After a brief introduction, the students then have time until the end of the term to solve a given task independently. Tutors will provide consultations and help the students.
Content
The module provides overview and special knowledge in the fields of design, simulation, and programming of modern embedded systems consisting of several processors and specialized accelerators. The exercises accompanying the lectures serve to strengthen the lecture material and provide practical experience in the above-mentioned subject area.
Qualification Goals
- Knowledge in the areas of design and programming of modern embedded systems
- Knowledge in the field of simulation of embedded multicore architectures
- Practical skills to use embedded operating systems, such as Embedded Linux or FreeRTOS, on a modern embedded system, such as the Xilinx Zynq System-on-Chip
Link:
Teaching Activities of the Chair for Adaptive Dynamic Systems
Content
The module provides overview and special knowledge in the fields of simulation, evaluation and verification of digital systems. The practical course accompanying the lecture includes practical experience in programming digital systems using the hardware description language VHDL and the modelling language SystemC.
Qualification Goals
After successful completion of this module, the participants have qualifying knowledge in the areas of simulation, evaluation and verification of digital systems, such as field programmable gate arrays (FPGAs), and in the area of modeling digital systems using SystemC. Further, they have practical skills in programming digital systems using the hardware description language VHDL and experience from sample projects.
Link:
Teaching Activities of the Chair for Adaptive Dynamic Systems
Microkernels are small operating-system kernels on which operating systems can be built flexibly. They are often used in real-time, security-sensitive, or embedded applications to provide a small system core for critical tasks, but can also be used to build well-structured general-purpose operating systems. This module teaches the construction of both microkernels and systems built on top of microkernels.
This module provides low-level insight in (not only microkernel-based) operatingsystems construction. We use a hands-on approach to systems teaching and use thesource code of real, working microkernels and operating systems. Topics in microkernel construction include CPU data structures, kernel entry and exit, system calls, virtualmemory management, inter-process communication, scheduling, threads, portability, and virtualization. Topics in operating-systems construction include system boot-up, high-level memory management, synchronization, interface description languages, device drivers, Linux on microkernels, multi-server operating systems, and real-time and secure operating systems.
Link:
Microkernel-based Operating Systems – Lecture Information
After successfully completing this module, participants will be able to develop programs with strong guarantees about their properties in order to minimize testing effort and avoid complex runtime errors during the development process. To this end, participants will know the basics of strongly-typed programming languages (dependently-typed languages) and their connection to logic. This knowledge enables participants to develop programs in programming languages such as Agda or theorem provers such as Coq and to formally prove their properties. Participants will know essential proof techniques to formally verify properties of programming languages, compilers, and even hardware-aware programs.
The module teaches the theories of the untyped and typed lambda calculus, as well as type systems with dependent types and their connection to propositional and predicate logic as the basis for the Curry-Howard isomorphism. The module also includes programming with strongly-typed programming languages, such as Agda, and theorem provers, such as Coq. On this basis, properties of programming languages and compilers and the possibilities to formally prove them in the design process of the same are discussed. Important proof techniques are introduced and the formal concepts for the description of the different semantic definitions (operational, denotational) are taught.
Links:
CPLCD – Foundations of Certified Programming Language and Compiler Design
Students get familiar with concepts and concrete designs of cooperative highly mobile systems, e.g. in networked road and air traffic. They are able to design such systems and evaluate their performance.
The module covers concepts, concrete designs and methods for the evaluation of cooperative highly mobile systems.
Students are familiar with concepts and concrete designs of networks in and from vehicles as well as of control units and their software. They are able to design vehicle networks and evaluate their performance and properties, especially with regard to security and privacy.
The module covers concepts, concrete designs and methods for evaluating networks in and from vehicles.
Links:
C2X – Vehicular Networking
After completion of this module, the participants have acquired technical, methodical, practical and interdisciplinary skills and possess initial abilities to work on a scientific topic of system architecture of their own choice in a research-oriented manner and, if necessary, to identify and solve problems in a team.
The module addresses the participants' individual interests in current and advanced content on topics related to the course of study, including operating systems, databases, computer networks, distributed systems and applications, data security, adaptive systems, and system architecture.
The module comprises lectures, exercises, practicals and seminars in the amount of 4 SWS as well as self-study. The courses are to be selected from the corresponding course catalog INF-DSE-20-E-ADSE to the extent indicated; this catalog, including the respective required examinations and the weighting of the grades of the examinations, is announced at the beginning of the semester as is customary for the faculty.
Link:
Course & Lecture Overview of the Faculty of Computer Science
After completion of this module, the participants are able to transfer the competencies acquired so far in the course of study to a topic unrelated to the subject or to an interdisciplinary topic (of their own choice) and to apply solution concepts in an interdisciplinary and domain-independent manner.
The module addresses the participants' individual interests in current and further contents on interdisciplinary or even non-disciplinary topics. Depending on the choice of the participants, the module includes the topics artificial intelligence, machine learning, multimedia technology, compiler construction or medical informatics.
The module comprises lectures, exercises, practicals and seminars in the amount of 2 SWS as well as self-study. The courses are to be selected from the corresponding course catalog INF-DSE-20-E-BDSE to the extent indicated; this catalog, including the respective required examinations and the weighting of the grades of the examinations, is announced at the beginning of the semester as is customary for the faculty.
Link:
Course & Lecture Overview of the Faculty of Computer Science
Compulsory Elective Language Modules
Aside from computer science, the DSE curriculum also includes language courses. You can choose either to learn (or improve) the German language or to improve (scientific) writing skills in English language.
This module aims provide you with the essential basics of the German language. You may choose one of the following German language courses from our language department.
Links:
Deutsch als Fremdsprache – A1
Deutsch als Fremdsprache – A2
Deutsch als Fremdsprache – A2+
This module aims to improve your English language skills. You may choose one of the following English language courses from our language department. Check their webpage for details regarding registration for language courses.
Links:
C1/C2 – Project Development and Administration
C1 – Advanced Professional Writing I
C1/C2 – Advanced Professional Writing II
C1+ – Academic Writing
C1 – Professional Communication in Science and Technology