Mehr-Faktor Authentisierung für das Admin-VPN
Inhaltsverzeichnis
Anwendungen
Hier wird die Nutzung der 2-Faktor Authentifizierung für IT-Administratoren der TU Dresden im VPN beschrieben.
Alle anderen TU Angehörigen finden die Hinweise zur Mehrfaktorauthentifizierung mittels Token in der FAQ des Ticketsystems unter:
https://tud.link/cvbf
zur Registrierung von Token gehen Sie auf diesen Link:
https://selfservice.tu-dresden.de/services/idm/token/
An der TU Dresden kommt 2-Faktor Authentifizierung für den VPN-Dienst des ZIH für IT-Administratoren zum Einsatz. Der Administrator authentifiziert sich über
VPN-GATEWAY : adminvpn.zih.tu-dresden.de
USERNAME : zih-login@Netzressource
PASSWORD : PIN@Einmalpasswort.
Weitere Einsatzmöglichkeiten sind:
- Integration in beliebige, bestehende Web-Applikationen
- Integration über Radius
- Integration über PAM-Modul
Anleitung für die Registrierung des Token
Bevor Sie den Token verwenden können, sind initial folgende Schritte notwendig:
- Beantragen Sie einen OTP-Token über eine Email an den servicedesk@tu-dresden.de Haben Sie den Token, dann...
- Öffnen Sie im Browser das Selfservice-Portal der OTP-Verwaltung über https://otp.zih.tu-dresden.de
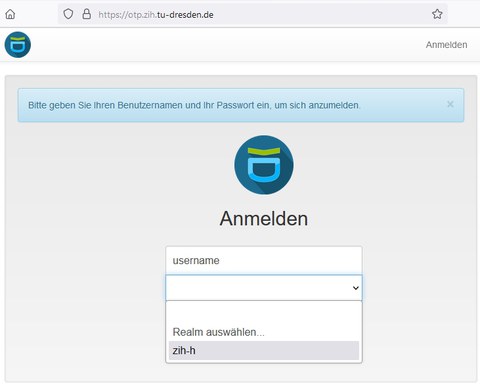
Selfservice Portal
- Wählen Sie zunächst den Relam "zih-h" aus, dann loggen Sie sich mit ZIH-Login und Passwort ein.
- Sie müssen Ihren Token registrieren. Dazu benötigen Sie die Seriennummer des Token, diese ist in dem Übergabeprotokoll, das Sie bei der Übergabe des Token vom ZIH erhalten haben, eingetragen.
- Klicken Sie bitte auf den Tab + Token zuweisen und tippen Sie die Seriennummer des Token in das entspechende Feld ein. Geben Sie in den Feldern unter PIN zweimal eine von Ihnen gewählte PIN ein (6-10 alphanumerische Zeichen, keine Sonderzeichen). Danach klicken Sie auf den Button Token zuweisen.
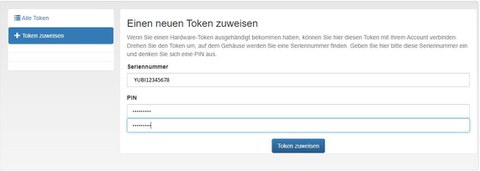
Token zuweisen
- Im Anschluss sehen Sie den Ihnen zugewiesenen Token:
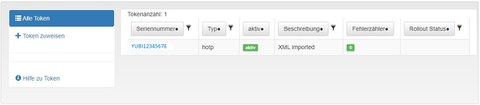
Token zugewiesen
- Klickt man in der Tokenansicht auf die Seriennummer des Token, dann werden die Details des Token angezeigt:
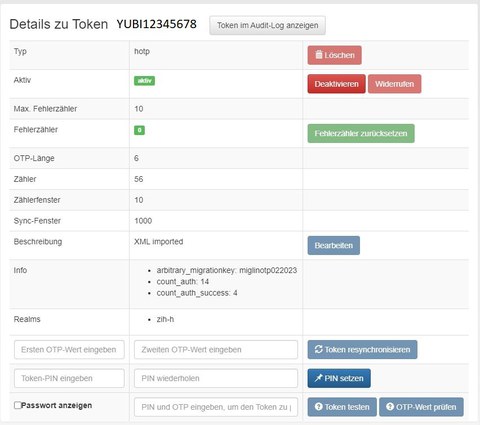
Details
- Nun müssen Sie noch den Token synchronisieren. Klicken Sie in der Detailansicht in der Zeile bei Token synchronisieren in das linke Feld Ersten OTP-Wert eingeben und drücken einmal auf den USB Token, danach in das Feld Zweiten OTP-Wert eingeben und nochmal auf den Token drücken. Danach auf Token resynchronisieren klicken:
- Danach sollte diese Ausschrift erscheinen:
- In der Detailansicht kann außerdem die PIN gesetzt werden: In der Zeile PIN setzen 2mal die Token PIN (Ziffern, Groß- und Kleinbuchstaben, 6 – 10 Zeichen) eingeben und auf das Feld [PIN setzen] klicken:
- ... und der Token getestet werden: Zum Testen im Feld neben Token testen erst die gesetzte PIN eingeben und ohne Trennzeichen gleich auf den YubiKey drücken.
- Danach auf [Token testen] klicken, es sollte diese Ausschrift erscheinen:
- Sie haben jetzt Ihren Token erfolgreich konfiguriert.
- Loggen Sie sich am OTP Selfserviceportal ab:
- Der YubiKey ist einsatzfähig, wenn die kleine grüne Lampe in der Mitte leuchtet.
FAQ
- Ich möchte meinen Token deaktivieren- ich habe meinen Token verloren/finde ihn nicht wieder/verlasse die TU Dresden
Bitte melden Sie sich im OTP Selfservice-Portal an und klicken Sie in den Token Details auf den Tab Token deaktivieren.
Wenn Sie Ihren Token verloren haben, melden Sie bitte den Verlust über
Wenn Sie die TU Dresden verlassen oder den Token nicht mehr benötigen, deaktivieren Sie diesen und geben ihn dann bitte an das ZIH zurück : ZIH Service Desk (gern auch per Hauspost)
Token deaktivieren
- Ich habe meine PIN vergessen bzw. möchte meine PIN ändern.
Bitte melden Sie sich im OTP Selfservice-Portal an und setzen Sie in der Token Detail Ansicht eine neue PIN, s.o. PIN setzen.
PIN setzen
- Ich habe bereits mehrfach auf den Button des Tokens gedrückt und kann mich nicht mehr anmelden.
Das Einmalpasswort muss synchron zum OTP-Server sein. Bei mehrfachem Drücken kann es vorkommen, dass das Einmalpasswort nicht mehr synchron ist. Sie müssen deshalb den Token resynchronisieren. Bitte melden Sie sich im OTP Selfservice-Portal an und führen Sie in der Token Detail Ansicht (s.o.) Token synchronisieren aus.

Token synchronisieren
- Ich habe den Token synchronisiert, aber es kommt immer wieder "Login failed". Das kann verschiedene Ursachen haben, u.a., dass der maximale Fehlzähler überschritten ist. Bitte wenden Sie sich an den
Fehler
Internal Server Error
- Lösung: laden Sie die Webseite neu, indem Sie oben links auf Aktualisieren klicken:
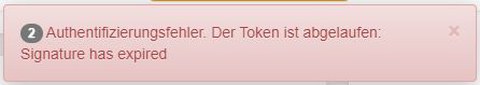
Authentifizierungsfehler
- Lösung: loggen Sie sich erneut auf der Webseite des otp-Serviceportals ein.
Tunnel-Groups
Beim Aufruf des Cisco AnyConnect können bei "Group:" verschiedene Tunnel-Groups ausgewählt werden. Diese werden hier erläutert:
- A-Tunnel-TU-Networks
Datennetzverbindungen in alle TU-Netze laufen durch den VPN-Tunnel, das sind:
141.30.0.0/16, 141.76.0.0/16, 172.16.0.0/12, 192.168.0.0/16 - B-Tunnel-Public-TU-Networks
Datennetzverbindungen zu öffentlichen TU-Netzen laufen durch den VPN-Tunnel, das sind: 141.30.0.0/16, 141.76.0.0/16 - C-Tunnel-All-Networks
alle Datennetzverbindungen laufen durch den VPN Tunnel - TUD-vpn-lic
Verwendung ausschließlich für den Zugriff auf den Lizenzserver (MathCAD u.a.)
Authorisierung über die DOM Domain (der Nutzer muss explizit durch seinen IT-Administrator in einer bestimmten ActiveDirectory Group der DOM Domain dafür eingetragen werden) - TUD-vpn-split-sap
tunnelt ausschließlich Verbindungen zu den SAP Servern der TU - Z-AdminVPN-dhcproute
tunnelt die internen TU-Netze wie A-Tunnel-TU-Networks, richtet keine Route zum DHCP Server des lokalen Netzes ein (no-dhcp-server-route) - wichtig für Admins, für den Zugriff auf Domaincontroller/DHCP-Server in MS Umgebungen - TUD-vpn-split-ivv, TUD-vpn-split-la-s, TUD-vpn-split-tk, Z-TUD-vpn-split-mgmt,
Tunnelgruppen für speziellen Einsatz
Token
Die Sicherheit bei der Benutzerauthentisierung kann deutlich erhöht werden, wenn mehrere Faktoren zur Anmeldung verwendet werden. Bei der 2-Faktor-Authentisierung werden "Besitz" und "Wissen" (Einmalpasswort) benötigt, um sich erfolgreich anzumelden. Ein Einmalpasswort ist ein Kennwort zur Authentifizierung, das nur für eine einzige Sitzung gültig ist. Jede Authentifizierung erfordert ein neues Einmalpasswort. Es ist somit sicher gegen Replay-Attacken. Bei einer starken 2-Faktor-Authentifzierung ("Wissen" und "Besitz") wird die Sicherheit deutlich erhöht, z.B. bei Einmalpasswortverfahren (OTP= ONe Time Password) in Verbindung mit einer PIN sowie einer Hardware (Token), die der Nutzer besitzen muss. Ein Hardware-Token ist ein kleiner elektronischer Schlüssel, den der Nutzer immer bei sich haben muss. Der Verlust eines Hardware-Tokens ist relativ unkritisch, da die PIN nur dem Nutzer bekannt ist. Bei mehrmaligen Fehlversuchen bei der Anmeldung wird der zugehörige Token automatisch gesperrt.
Als Plattform für die starke 2-Faktor-Authentisierung wird die Lösung privacyIDEA OTP zur Authentifizierung über Einmalpasswörter sowie PIN (Wissen) und Hardware-Token (Besitz) eingesetzt.
Z.Zt. werden die Hardware-OTP-Token vom Typ eToken PASS der Firma SafeNet und YubiKey Token der Firma yubico eingesetzt, weitere Token-Formate sind möglich. Nach Betätigen des Knopfes auf dem Token wird ein Einmalpasswort (OTP) generiert. Technisch basieren die von den Token erzeugten Einmalpasswörter auf dem Open Authentication Standard (OATH), einem zertifizierten und weltweit anerkannten Verfahren.
Der YubiKey ist ein schmaler, flacher USB-Token, der über den USB-Port mit Strom versorgt wird und ohne Batterien auskommt. Die Lebenszeit ist daher theoretisch unendlich. Das Betriebssystem erkennt den Yubikey als USB Keyboard, es ist also keine Installation einer Client-Software notwendig. Zur Authentisierung wird der Cursor auf die Anmeldemaske bewegt, eine leichte Berührung der Sensorfläche des Tokengehäuses genügt - der Yubikey generiert das Einmalpasswort und setzt es automatisch ein.